WALLET RECOVERY SEED - BACKUP SECURITY SOLUTIONS
The importance of proper backup security for your wallet recovery seed:
 Every crypto wallet has a backup seed. Making sure this wallet backup is secure is primordial. The backup or recovery seed consists of 12 or 24 words you receive during the wallet installation and setup procedure. It is the mnemonic phrase, and with some effort you could easily remember it. Most people do'nt trust their memory; so normally, these words are written down on a thin carbon board paper. This is often included in the package of a hardware wallet like the Trezor. In the case of other wallets you will probably have to grab a paper or notation book for recording the words. These words, how insignificant they seem to be, are in fact the most precious words you write down. Losing these words is equal to losing access to your crypto funds if your wallet crashes or get damaged. Without these words you will never be able to recreate your wallet. Indeed, it is this recovery seed or wallet backup seed you need to protect and safeguard the best you can. Over time wallets do crash and malfunction. Your computer could crash as well. That’s why you have to realize that you will use the recovery seed from time to time. Now, writing the recovery seed of your wallet down on a paper or a piece of carbon is not what we would call optimal recovery seed security.
Every crypto wallet has a backup seed. Making sure this wallet backup is secure is primordial. The backup or recovery seed consists of 12 or 24 words you receive during the wallet installation and setup procedure. It is the mnemonic phrase, and with some effort you could easily remember it. Most people do'nt trust their memory; so normally, these words are written down on a thin carbon board paper. This is often included in the package of a hardware wallet like the Trezor. In the case of other wallets you will probably have to grab a paper or notation book for recording the words. These words, how insignificant they seem to be, are in fact the most precious words you write down. Losing these words is equal to losing access to your crypto funds if your wallet crashes or get damaged. Without these words you will never be able to recreate your wallet. Indeed, it is this recovery seed or wallet backup seed you need to protect and safeguard the best you can. Over time wallets do crash and malfunction. Your computer could crash as well. That’s why you have to realize that you will use the recovery seed from time to time. Now, writing the recovery seed of your wallet down on a paper or a piece of carbon is not what we would call optimal recovery seed security.
Best solution for wallet backup protection and recovery seed security:
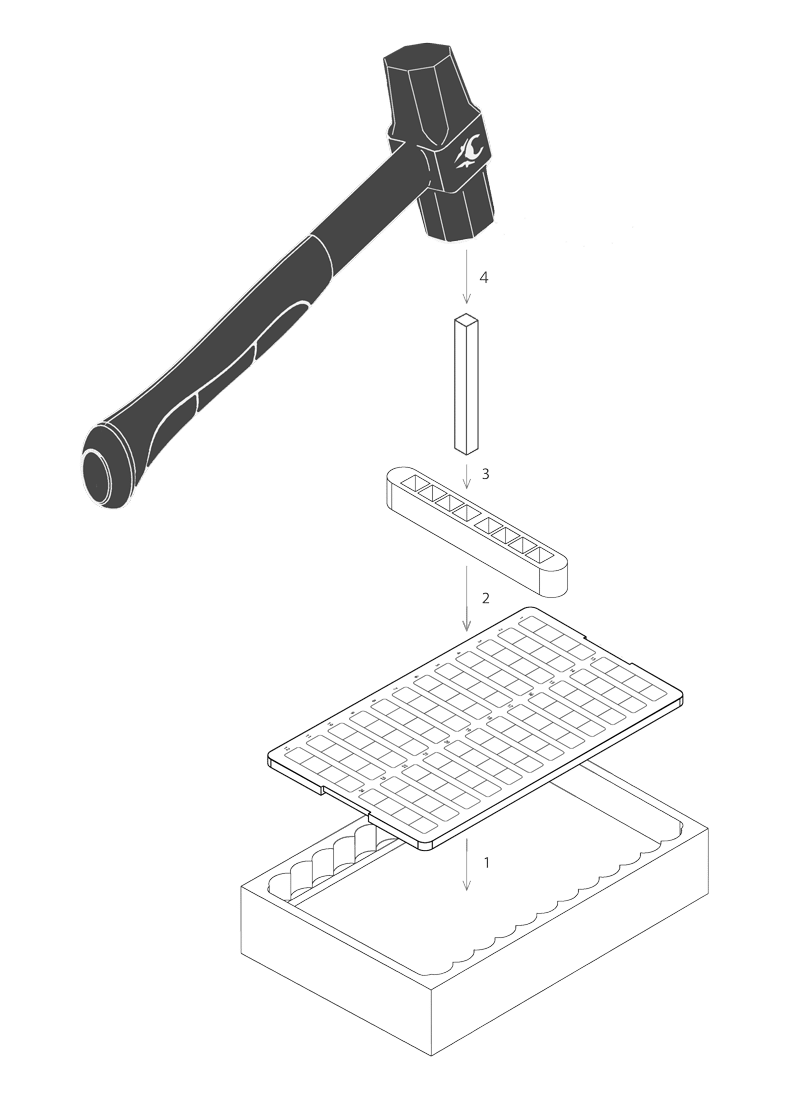 The best solution for protecting your wallet backup and security seed is the CRYPTOTAG. It is the best and easiest to use wallet backup security solution. It makes sure your crypto recovery seed and private keys are forever stored in pure Titanium. The CRYPTOTAG perfectly engraves your private key backup in the titanium with a few simple hammer strokes. You have to follow four simple steps:
The best solution for protecting your wallet backup and security seed is the CRYPTOTAG. It is the best and easiest to use wallet backup security solution. It makes sure your crypto recovery seed and private keys are forever stored in pure Titanium. The CRYPTOTAG perfectly engraves your private key backup in the titanium with a few simple hammer strokes. You have to follow four simple steps:
- Place the CRYPTOTAG Plate in the Anvil.
- Place the Bit Holder on the row you want to enter your recovery words.
- Place the Bit with the correct letter inside Bit Holder.
- Hammer time! Give the Bit a smash with the hammer to perfectly engrave the letter, forever in Titanium.
All required items are included with the CRYPTOTAG. For more information:
Best wallet backup security for your recovery seed:
If you are storing a lot of value you might consider to buy four Cryptotags and split the words over the first two and store them on seperate locations. You repeat this again for the other two. Now you have made two safe splits of your private key, and in the event of theft you are sure the the thieve has no way to restore your private key with help of the recovery seed as it only contains 12 of the 24 words in case you are using the Trezor hardware wallet.
What is the difference between the recovery seed and a private key?
The recovery seed in the form of a mnemonic phrase (N words) is just one way to encode a private key (aka seed). In fact you could consider it as the initial principal founding private key for your wallet. While technically there is an intermediate "ECDSA private key" state generated by seed-based private keys, this intermediate state is merely an implementation detail and not different in any useful sense: if someone gets the ECDSA private key for any part of the wallet, your entire seed is essentially compromised. Thus, the seed is itself really the only relevant private key. It is responsible for generating all (public and private) keys in your wallet.
For example, your Bitcoin wallet is a Deterministic wallet. If you want to maintain anonymity on the Bitcoin network, it is suggested that you use a new address each time. So each time when you create a new public address, it’ll come with a private key. Each private key associated with a public key (the address) lets the user access the funds which are accumulated in the address given by the public key. Suppose your wallet was a Non Deterministic wallet. In this case, if you were to create a new address for each deposit that you receive, you’d create as many private keys as public keys. Thus if you were to back up this wallet, you’d need to store all these private key - public key pairs.
Instead, you could use a Deterministic wallet. A deterministic wallet uses a seed key which is used to generate all subsequent public key - private key pairs. This seek key is fetched using the seed words that you get when creating or backing up your wallet. So now, you can create as many new addresses on your wallet as you want but when you back up your wallet, all you need to store is the set of seed words. When you restore your wallet, enter these seed words and your wallet will automatically create all the public key - private key pairs you own and give access to all your funds.
In summary, a the private key is what lets you access the funds associated with one public address in your wallet. But when you create new public addresses for each new deposit to your wallet for security reasons, it also creates a new private key which means when you backup your wallet, you’ll have to save all these public key - private key pairs. Instead if your wallet is Deterministic, you could simply use the seed words to restore your wallet. Seed words can be used to programatically generate all the public key - private key pairs you own.

Every time you set up a new wallet, protecting the initial principal founding private key (aka the recovery seed represented in a mnemonic phrase) should be on top of your priority list.
Security and privacy are always for every crypto investor top priorities. Mistakes eventually lead to loss of funds.
This important knowlegde means you need to do the following if you want to invest safely in Bitcoin or any other cryptocurrency:
- You should invest in a hardware wallet which shows the mnemonic phrase (N words) on it's own screen. Therefore potential malware on the computer can't intercept this vital information. Recommended solutions: Trezor and Ledger.
- You should invest in a recovery seed security solution. Recommended solution: CRYPTOTAG.
- The use of VPN software is as well highly recommend in order to encrypt your internet connection and communication. Recommended solution: Trust Zone VPN.
- The use of email aliases for important (crypto exchange) accounts.
We hope this information will help you to revisit your own crypto security setup .
Related article:
Spanish version:
Sources:


